We provide Direction
Cyber Security a Dynamic and Evolving Field
Cyber Security Consulting
The continuous and evolving nature of cyber security in organisations.
- Consider that cyber security is an ongoing process, and the threat landscape is constantly evolving.
- Regularly reassess and adapt your security measures to address new challenges and emerging threats.
- Additionally, having a cyber security professional or team in place can enhance your organisation's ability to stay ahead of potential risks.
Cyber Security Road map
- Creating a cyber security road map is essential for organisations to pro-actively address security threats and vulnerabilities
- A cyber security road map serves as a strategic plan that aligns security efforts with organisational goals, helps organisations identify and mitigate risks, and ensures compliance with relevant regulations
- It is a proactive approach to cyber security that benefits the organisation's financial stability, reputation, and long-term success
There is a convincing need to adapt as the threat landscape evolves and the organisation's needs change.
Challenges in Producing your Cyber Security Road map
Creating a cyber security road map for your organisation
Key considerations
- By following a structured approach cyber security, your organisation can maintain accurate records, demonstrate compliance, improve your cyber security stance, and effectively manage security-related activities and changes
- Remember that cyber security is an ongoing process. Regularly review and update your road map to stay ahead of emerging threats and evolving security requirements
Collaboration between IT, security teams, and senior management is crucial to the success of your cyber security road map
More information...
about creating your organisations cyber security road map can also be found in this textbook on Amazon...

Why is it important for you?
Cyber-crime can cause significant damages to organisations, including (but not limited to):
- Financial Loss
- Data Breaches
- Reputation Damage
- Legal and Regulatory Consequences
- Operational Disruption
- Intellectual Property Theft
- Extortion
- Supply Chain Disruption
- Loss of Customer Trust
- Liability
- Regulatory Fines
- Business Disruption
- Fraud
- Environmental Damage
- Identity Theft
- Loss of your business altogether
How can Cognicions help your organisation?
- Providing guidance on establishing your cyber security management, framework, policies, and procedures
- Assist with delivery of governance and compliance requirements
KEY SERVICES
- Program / Project Management
- Governance
- Cyber Project Definition
- Establishment of Cyber Security Road map
- Cyber Policies and Procedures
- Risk Management review
Common cyber security threats
Cyber security threats are diverse and continually evolving as technology advances. Here are some common cyber security threats that organisations and individuals often face:
- Ransomware
- On-line shopping
- Phishing emails and texts
- Business email compromised
- Data breach
- Quishing
- Malware
- Distributed Denial of Service (DDos) Attacks
- Man-in-the-Middle (MitM) Attacks
- SQL Injections
- Cross-Site Scripting (XSS)
- Zero-Day Exploits
- Password Attacks
- Social Engineering
- IoT Bulnerabilities
- Credential Stuffing
- Insider Threats
- Supply Chain Attacks
Staying informed about these common cyber security threats and implementing proactive security measures can help your organisation mitigate risks and protect against potential cyber attacks.
Prevention methods:
- Set up a cyber framework
- Establish cyber treatment policies and procedures
- Have a plan of action to remedy if attacked
- Update your devices
- Set up and perform regular backups
- Turn on multi-factor authentication
- Set secure passphases
- Recognise and report scams
- Watch out for threats
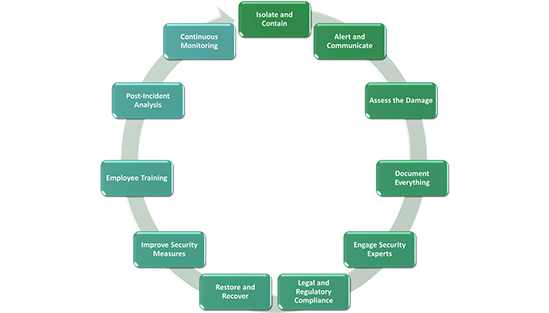
A suspected or confirmed cyber-attack, what do you do next?
If you suspect or confirm that a cyber-attack has occurred, it's important to respond promptly and effectively to minimise damage and protect your systems.
Here is a general guide on what to do in the event of a cyber-attack:
Remember that every cyber-attack is unique, and the specific steps you take will depend on the nature and scope of the incident. If you're unsure about how to proceed, it's crucial to consult with cyber security professionals who can provide guidance based on the specifics of your situation.
Key Outcomes:
Here are some key principles and practices to achieve more effective and predictable cyber security outcomes:
- Remember that cyber security is an ongoing process, and the threat landscape is constantly evolving.
- Regularly reassess and adapt your security measures to address new challenges and emerging threats.
Additionally, having a cyber security professional or team in place can enhance your organisation's ability to stay ahead of potential risks.
Protect your business from evolving cyber threats with our comprehensive Cyber Security Consulting services.
We provide risk assessments, threat management, and compliance solutions to safeguard your data,
secure your infrastructure, and enhance your organisation's resilience.
© Cognicions Pty Ltd 2015-2025 All Rights Reserved
Custom Business Software
DISCOVERY
Our Clients
Our Team
Careers
Request a Quote
Engagement Process
Approach
Contact
Contact Form
Terms & Conditions
Privacy Policy
Cyber Security